Industrial IoT Security: Top Priority for Industry 4.0 Systems
Insights | 23-08-2024 | By Gary Elinoff

Industrial Internet of Things Security
Key Takeaways about Security: Priority Number One for the Industrial Internet of Things
- The Industrial Internet of Things (IIoT) is the driving force behind Industry 4.0.
- The actual differences between the IIoT and the Internet of Things (IoT) are nebulous.
- There is nothing so vital to a safe and effective IIoT installation as security.
- Security is complex and difficult to achieve. It can’t be dealt with as an afterthought but must be a prime concern throughout the entire system design process.
Introduction
The first factories were controlled mechanically by men with hammers and wrenches. Later on came electrical control, and when those electrical actuators were superseded by electronic devices, those devices were still controlled locally, even if by various types of computing devices. Then came computer networking. But even here, the protocols were individualistic and not well known; the famous Arpanet was an early example. Additionally, the lines themselves were often isolated and proprietary.
Then came the Industrial Internet of Things, (IIoT), which involves using the same very vulnerable cloud-based internet over which you are reading this article, purposed to operate and control everything from factories, supply chains and energy networks to military drones. The result was, and is, an epidemic of hacking, with outside malefactors breaking into networks, stealing information and sometimes even stealing control.
The IoT differs from the Industrial Internet of Things (IIoT) largely on the basis of the need for system reliability. As described in a previous Electropages article, IIoT Basics and Key Benefits of Industrial Internet of Things, we refer to the IoT when we describe consumer-based systems, such as the system that amalgamates a smartwatch to a smartphone, recording a runner’s heart rate for the course of their workout. No great tragedy occurs if a jealous neighbor hacks into the system and learns all about your workout results or even if they cause the report to never reach your smartphone.
The system that monitors and controls the warehouse’s inventory is referred to as the IIoT. Here, failure costs money, lots of it. Same thing for the IIoT system that controls a bank’s network of ATMs.
Other examples require greater reliability still. For example, the one thing that today’s Western all-volunteer militaries can’t do is take casualties, so as much as possible, unmanned systems are relied on, with 6th generation aircraft being prime examples. These unmanned drone aircraft are controlled remotely by pilots on the far periphery of the combat theatre, enjoying relative safety. Imagine the catastrophe that would occur if an enemy were to take control of an Allied drone system. Here, IIoT network security represents the very highest order of necessity.
The growing dependence of the military on IIoT systems of all sorts absolutely mandates that network security is today the very most important thing on the mind of systems designers.
IT vs OT
OT stands for Operational technology, a network that controls a physical system. IT is the more familiar informational technology. They evolved separately, and as we’ll see, the consequences of each being hacked were different, so as separate entities, they have needs for different levels of security.
There are still IT only systems, and plenty of them. But OT is gradually embracing IT, and together they are the basis of Industry 4.0.
IIoT Security Planning
As described In a blog published by the ISA Global Cybersecurity Alliance[1], the Purdue Model, based on the ISA/IEC 62443 standard, has been a basic model used to explain and implement IIoT security.
This model differentiates between systems that merely monitor from those that not only monitor but also control. If one of the former is compromised, there are the ordinary business risks of the wrong people gaining access to sensitive information. For the systems that monitor and control, there can be very real and immediate physical consequences, hence the need for higher security.
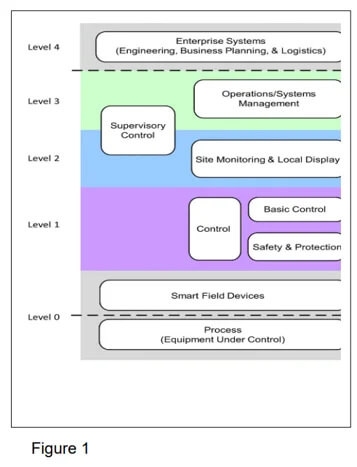
The Purdue Security Model. Image source: ISA Global Cybersecurity Alliance
Another hallmark is segmentation, which can be thought of as an IT version of the isolated bulkheads found in large oceangoing vessels. In the latter, if one portion of a ship is flooded, physical isolation barriers will contain the inrush of water to only one segment of the ship. Under this scenario, the damage is localized, the ship as a whole is saved, and efforts can be made to reverse the damage. In IIoT systems, the bulkheads are electronically based, and in a similar manner, the breach is localized, and the system as a whole may be compromised but not destroyed.
Enhancing Security
Access Control
Access Control is a key factor in enhancing security, and as described by the National Institute of Standards and Technology (NIST) an important requirement is for a Physical Access Control System (PACS).

A PACS implementation. Image source: NIST Special Publication NIST SP 800-82r3
Authentication
NIST[2] places much emphasis on multilevel authentication, both on a physical level and for software and network interactions. Each layer of the system must present a separate requirement for specific area-level authentication. Multi-factor authentication is highly recommended.
Encryption
Data should be encrypted to prevent unauthorized access when data is in transit. Stored data must also be encrypted, so if an attacker gains access, the malefactor faces the additional hurdle of unencryption if they are to gain from their attack.
The downside of encryption is latency because the encryption/unencryption cycles will invariably take time, slowing down the overall responsiveness of the system.
OT Cybersecurity Best Practices
IIoT World[3] describes important elements of cybersecurity management.
- Network Mapping. Knowledge of where on the network elements are located and to which other elements they are connected to. This makes it easier to mitigate the results of any cyber attack.
- Defining threat types and quickly responding to them. This can be aided through the use of a firewall to detect potentially harmful data packets and then block them.
- Zero Trust. Every interface to the network, human or electronic, must provide proof of its validity before it can gain any sort of network access.
- Provide remote access tools. Unlike Informational Technology (IT) systems, Operational Technology (OT) systems that control machine systems generally include less native provision for protected remote access. That deficiency must be corrected.
Software Supply Chain Attacks
It’s vital for technical management to continuously make itself aware of the current threats menacing IT and OT systems.
Software supply chain attacks are increasingly threatening. They occur when the malevolent element is carried into the system by a seemingly innocent software update, chillingly reminiscent of a biological virus introducing dangerous DNA/RNA into a previously healthy living cell.
Software Bills of Materials (SBOM) are detailed compendiums of all software elements and their interrelationships. It includes license and version data, including possible vulnerabilities. They can help avoid supply chain attacks, such as the recent Solar Winds fiasco.
Perimeter security, guarding the overall access to the system, is a key element in network security. It is a vital element in guarding against supply chain attacks in particular.
Security at the Edge
In a previous Electropages article, What is Edge Computing? The Future of Real-Time Data Processing, we describe systems where decisions are made at the actual point where the IIoT control system actually meets the electromechanical system that it is monitoring and controlling. Decisions are often made with the help of local AI.
With edge computing, there is no need to utilize the internet to access remote servers. This deprives hackers of their greatest opportunity, and security is far easier to maintain.
Challenges and Opportunities
Artificial intelligence is a powerful tool in the system designers security arsenal. This powerful methodology can be taught to recognize attack vectors, and to nullify them. The use of AI is becoming more and more important in this endeavor.
Throughout the industrial world, and in those parts of the world with the potential to industrialize, populations are shrinking. The cadres of working-age people are shrinking even faster, but the one thing that isn’t shrinking is the need for goods and services, so producers of all sorts will have to do more with less, and that’s where the IIoT comes in.
Similarly, it’s getting increasingly difficult for Western militaries to recruit soldiers, sailors and airmen, so military leaders, too, must rely increasingly on automation. The consequences of a breach into Western military weapons systems are too horrible to contemplate.
For these reasons and more, security can no longer be an afterthought, to be tackled last after everything else is done. It has to be JOB ONE, built from the ground up and the very first consideration.
Wrapping Up
The differences between the IoT and The IIoT come down to how dire the consequences of a breach are. A breach affecting the connection between a jogger’s smartphone and their mobile app is inconsequential, but an intrusion between a manned fighter plane and a 6th generation drone could potentially alter the course of a war and maybe history itself.
Edge computing, particularly security at the edge, is a powerful tool in the arsenal of the security designer, because decisions are taken locally, with no reference to the internet, cutting off the main avenue that hackers might otherwise employ to effect cyber attacks.
For these reasons and more, Western governments are publishing guidelines and standards that potential vendors, as well as every other IIoT developer, needs to heed.
Edge computing, particularly security at the edge, is a powerful tool in the arsenal of the security designer because decisions are taken locally, with no reference to the internet, cutting off the main avenue that hackers might otherwise employ to affect cyber attacks.
References
- IIoT Cybersecurity Explained: https://gca.isa.org/blog/iiot-cybersecurity-explained
- Guide to Operational Technology (OT) Security, NIST Special Publication NIST SP 800-82r3: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-82r3.pdf
- Best Cybersecurity Practices for the IT/OT Environment: https://www.iiot-world.com/ics-security/cybersecurity/9-best-cybersecurity-practices-itot-environment/
Glossary of Key Terms
- IT: Informational Technology. An attacker gaining access to an IT center gives them unauthorized access to data but no immediate ability to do actual physical damage.
- OT. Operational technology. An attacker gaining access here has the opportunity to do real physical damage to a power system or, perhaps, a system of Iranian uranium enrichment centrifuges.

