Edge Computing – The Future IoT Solution
03-04-2020 | By Robin Mitchell
The field of IoT has seen a dramatic rise of internet technologies being integrated into everyday life. However, the lack of security has resulted in social pressure and government action forcing designers to implement stronger security features. How can edge computing help and why may it become the ultimate solution for IoT in the future?
Introduction
Since their introduction, IoT devices have exploded globally with an estimated number of at least 20 billion globally. While the term Internet of Things, or IoT, is a relativity new term the use of internet related technologies dates back to the creation of the internet itself. But the IoT movement is more concerned with simple devices that traditionally would not have internet capabilities (such as sensors and data loggers) which is why it is considered a separate sector to standard internet computing technologies such as computers, laptops, and phones.
The first IoT devices were simple in nature and often targeted for niche markets including basic remote temperature and humidity logging. As the nature of the data that was being gathered was benign in nature (i.e. not sensitive), security was given the minimal concern with many devices using default passwords and unencrypted messaging protocols. Since the number of IoT devices at the beginning was minimal combined with the lack of capabilities these devices went unnoticed by security experts, cybercriminals, and governments alike. But all of this changed as technology improved, devices became more intelligent, and the nature of the data being gathered became more sensitive.
Rise of Sensitive Data
One technology that has accelerated thanks to the IoT sector is AI thanks to the unimaginable quantities of data provided by IoT devices. AI systems are being used to power many modern tasks that are otherwise too difficult or too varied to be programmed traditionally using if statements and switch cases to account for every possibility. Such examples would include speech recognition, voice recognition, image recognition, intelligent search results, and personalised assistants. As stated previously, the first data types gathered by IoT were benign in nature including temperature and humidity which could be use to create intelligent systems that can respond to those environmental stimuli. But designers quickly realised that with the advancements in microcontroller technologies (for example, the shift from 8-bit to 32-bit ARM) more complex data types could be gathered including audio and visual. Such systems could be used to create advanced AI IoT devices that could not only gather data about their surroundings but send this data to a cloud-based AI system which can learn from the data and provide better results in the future. For example, the Amazon Echo is an IoT device that submits spoken user requests to a cloud-system which is analysed for both performing the request as well as improving the AI for future use. Very quickly, IoT devices exploded globally containing a whole range of integrated features ranging from accelerometers, magnetometers, motion sensors, cameras, and microphones. But the speed at which these devices were being designed and put to market was far too great and this is where cybercriminals began to take advantage.
The speed at which IoT designs changed as well as the sudden increase in demand for IoT devices saw engineers turn around products in record time. This, combined with the inability of governments to respond to fast changing markets as well as the short-sightedness of designers quickly saw many billions of devices on the market that contained insufficient security measures while handling highly sensitive data. It would not be long before cybercriminals used the many weaknesses of IoT devices to perform malicious activities including DDoS attacks, crypto-mining, blackmail, and data selling. Devices on the market would either have a default password or no password, would not use encrypted messaging protocols, would be built on unsecured silicon technologies, or would leave admin privileges in place for the application space (i.e. the firmware would run with full processor privileges). Devices could also leave networks exposed by allowing an attacker to gain easy entry to the device and then utilising its network connection to either gain internet access or local access (which could allow it to gain entry to servers and other devices on the same network).
Despite warnings from security specialists and others in the industry governing bodies around the world have begun to introduce regulations that describe how designers should remove features that leave their designs open to easy attack. So far, the majority of these regulations are more concerned with removing default passwords but as time progresses these may change to include more features such as mandatory encryption, on-device hardware security, and the need for security when the device is decommissioned. However, there is one emerging technology that may help to solve issues with IoT security; edge computing.
Introduction to Edge Computing
Currently, IoT devices gather data from their surroundings and stream this data to a cloud-based platform which in-turn can provide multiple features including data viewing, data learning, and data processing. For example, an advanced home automation system might have various IoT sensors around a property whose data is streamed to a cloud-based service that determines how environmental controls should be adjusted. This use of the cloud to perform data processing is often called “cloud-computing” and essentially means that the data processing is done remotely from the IoT device responsible for gathering that data. Edge computing, however, is where the IoT device itself is responsible for some proportion of data processing either partially or entirely. Early IoT devices would not be capable of edge computing due to the limitations of technology at the time but with the introduction of powerful microcontrollers at equivalent prices local IoT devices can start to process their own data.
Advantages of Edge Computing
Edge computing holds a lot of advantages over cloud-computing including security, latency, and reliability. Since edge computing devices transmit little data to a cloud-based system (if at all) sensitive data is less exposed to potential sources of attacks. The lack of transmission means that an attacker would need to gain direct entry to the device itself as opposed to performing a man-in-the-middle attack, an attack on the server itself, or spoofing the server. Keeping data local to a device also provides designers with more opportunity to protect the data as soon as it is gathered with the use of memory encryption as well as dedicated security hardware. Edge computing devices can also perform partial processing on sensitive data before sending it to a cloud-based system for further processing which can help obscure data and thereby reducing its usefulness to an attacker (i.e. a trained neural net is far less sensitive than visual data from a camera).
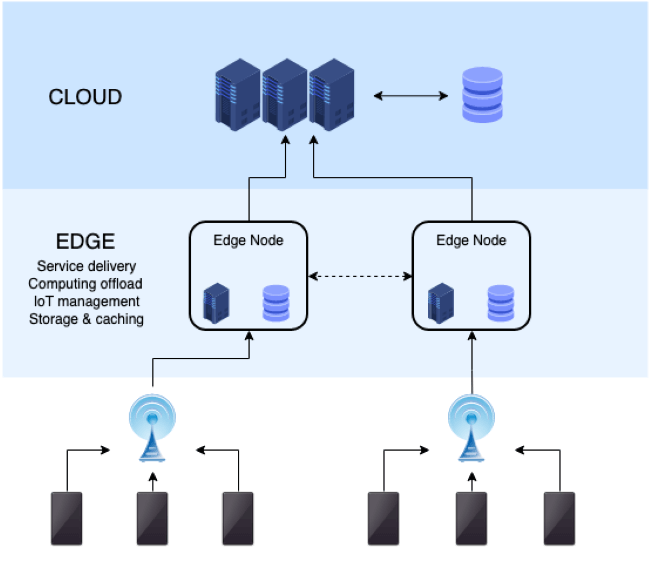
Processing data itself locally to a device also means that latency is significantly reduced which is highly beneficial in applications requiring fast results (such as self-driving cars). The ability to locally process the data also removes the need for a constant internet connection which helps to improve reliability of the design. Many areas globally still suffer from internet reliability and can also be subjected to large swings in internet speed. The use of edge computing helps to increase the available bandwidth of a local network which can improve other services such as local servers and other IoT devices and therefore increase the maximum number of devices on a single network (thereby allowing for more IoT devices to be integrated).
Disadvantages of Edge Computing
While the cost of micros has continued to fall while their capabilities have significantly increased they are still more expensive than cheaper microcontrollers making low-end micros more desirable for mass-produced devices. The introduction of regulations also makes it harder to use mid-range devices that have the processing capabilities needed for advanced features as they may lack hardware security that could leave them exposed. At the same time, the need for AI in modern products also further limits the choices for engineers who may need AI engines on their IoT devices to efficiently run neural networks.
Conclusion
Edge computing provides designers with a whole new paradigm of computing that can see low-latency, high reliability IoT devices that can combine the best features of cloud-computing with local processing. Hardware security features such as secure boot and root-of-trust will become key technologies for securing devices and the inclusion of AI engines will allow devices to perform the majority of data processing locally. But despite the many security advantages provided by edge computing designers still need to carefully consider how their device handles sensitive data, how it can potentially be used maliciously, and how they can help to not only protect the users but also contribute to the world stage in an ever more interconnected future.

